Introduction
These blogs are focused primarily on understanding the Windows Active Directory environment and seeing it from different point of views i.e. as an Administrator who tries to add security policies to harden the environment and an attacker who tries to bypass that and uses the same policies to manipulate the environment, and as a defender who tries to detect these attacks. There are many things that lead to the compromise of Active Directory, like misconfigured settings, poor maintenance procedures, and many other mistakes made by administrators. It may be little lengthy covering the basic and advanced concepts, environment setup and understanding attacks, but this will be helpful in enumerating the environment and simulating different attacks as one would do when doing a Red Team or penetration testing assessments.
Active Directory
The simple definition of Active Directory would be a service by Microsoft which acts as a centralised repository and stores all the data related to objects like Active Directory users, computers, servers, and other resources within an organisation and it makes administration and management easy for the System Administrators. But its primary function is to provide a way to authenticate users and machines in a domain environment. Using Active Directory, resources like users, workstations and their permissions can be managed remotely. Hence it’s a single management interface that is accessible from anywhere on the network. It is a feature of Microsoft Windows primarily, but other operating systems can also participate in it to a limited degree, for example you can join a Linux-based host in an Active Directory environment.
Domain
In simple words, a domain can be called as a collection or structure of all Active Directory objects like users, computers, groups etc sharing a common Active Directory database and is managed by main server of the domain which is called as a Domain controller. A domain is always referred to by its unique name and has a proper domain name structure.
Example of a domain name is rootdse.lab.
ROOTDSE in this domain name represents its NetBIOS name
We can split up an Active Directory infrastructure into separate domains to create smaller boundaries so that the administration tasks for different domains can be segregated within a large-scale network. In an Active Directory environment, domains also create a boundary for managing certain settings such as password policies and account lockout policies so that they can be applied only to domain user accounts at the domain level. We will talk more about the Group policies and misconfigured policies later in this series.
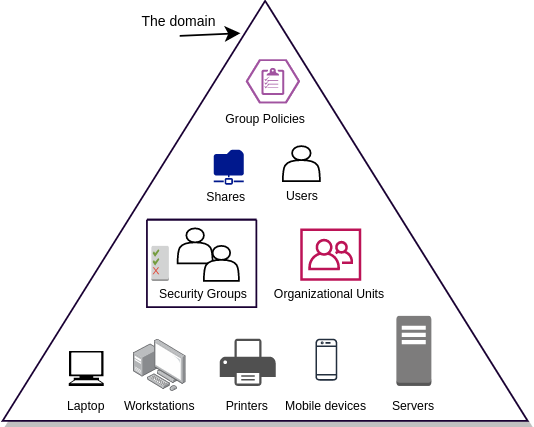
Below are few important components that are included in a domain:
- Objects like Groups, Users, Computers etc.
- Authentication service
- Group policies
- DNS
- DHCP
Active Directory Powershell Module
By importing the Active Directory Module in powershell, we can retrieve basic information about the Domain environment.
Active Directory module is present by default in domain controllers, but not on workstations.
This is the location of the file on a DC:
C:\Windows\Microsoft.NET\assembly\GAC_64\Microsoft.ActiveDirectory.Management\
By default, this module needs Remote Server Administration Toolkit (RSAT) to be installed on the client machine (where you want to enable Active Directory powershell module) which requires Administrative privileges. Every domain controller has RSAT installed. So domain controllers and member servers have built-in Active Directory module installed. But there is a way to use it on workstations as well (without installing RSAT) by just copying the DLL file from domain controller and import it in powershell session.
To import it on domain joined workstations, download it from here and import it simply by using Import-Module and then any command from this module can be used.
Import-Module '.\Microsoft.ActiveDirectory.Management.dll'
To retrieve the information about the domain, we can use below command:
PS C:\Users\scarred.monk> Get-ADDomain
AllowedDNSSuffixes : {}
ChildDomains : {matrix.rootdse.lab}
ComputersContainer : CN=Computers,DC=rootdse,DC=lab
DeletedObjectsContainer : CN=Deleted Objects,DC=rootdse,DC=lab
DistinguishedName : DC=rootdse,DC=lab
DNSRoot : rootdse.lab
DomainControllersContainer : OU=Domain Controllers,DC=rootdse,DC=lab
DomainMode : Windows2016Domain
DomainSID : S-1-5-21-580985966-2115238843-2989639066
ForeignSecurityPrincipalsContainer : CN=ForeignSecurityPrincipals,DC=rootdse,DC=lab
Forest : rootdse.lab
InfrastructureMaster : RDSEDC01.rootdse.lab
LastLogonReplicationInterval :
LinkedGroupPolicyObjects : {CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=rootdse,DC=lab}
LostAndFoundContainer : CN=LostAndFound,DC=rootdse,DC=lab
ManagedBy :
Name : rootdse
NetBIOSName : rootdse
ObjectClass : domainDNS
ObjectGUID : 70b22e8c-d4e3-4690-b4e0-0998b0125fb2
ParentDomain :
PDCEmulator : RDSEDC01.rootdse.lab
PublicKeyRequiredPasswordRolling : True
QuotasContainer : CN=NTDS Quotas,DC=rootdse,DC=lab
ReadOnlyReplicaDirectoryServers : {}
ReplicaDirectoryServers : {RDSEDC01.rootdse.lab}
RIDMaster : RDSEDC01.rootdse.lab
SubordinateReferences : {DC=matrix,DC=rootdse,DC=lab, DC=ForestDnsZones,DC=rootdse,DC=lab, DC=DomainDnsZones,DC=rootdse,DC=lab, CN=Configuration,DC=rootdse,DC=lab}
SystemsContainer : CN=System,DC=rootdse,DC=lab
UsersContainer : CN=Users,DC=rootdse,DC=lab
To retrieve the domain name, we can use below command:
PS C:\Users\scarred.monk> (Get-ADDomain).DNSRoot rootdse.lab
SID
Every domain has a unique SID (Security Identifier) with which it is identified. Generally, SIDs are used to uniquely identify security principals like user accounts, computer accounts or processes running in security context or a user or computer account. SIDs are unique within their scope (domain or local), and they are never reused. For domain accounts, SID of a security principal is created by concatenating the SID of the domain with a relative identifier (RID) for the account.
RID
RID (Relative identifier) is a part of an Active Directory object’s Security Identifier (SID) that uniquely identifies an account or group within a domain. It is assigned to active directory objects at the time of creation. RID is the last part of a SID.
FQDN (Fully Qualified Domain Name)
Fully Qualified Domain name is the complete domain name for a specific host in a domain.
FQDN contains two parts: Hostname + Domain name
For example, If a domain is matrix.rootdse.lab, and a computer in the matrix domain has hostname MTRXDC01, then the FQDN of that computer would be mtrxdc01.matrix.rootdse.lab
Domain Controller
In simple words, Active Directory Domain Controllers host the service that responds to the authentication requests in a domain. It authenticates and validates the user access on the network. When user and computer accounts sign into the network, they authenticate to domain controller that validates their information like username, password and then decides whether to allow or deny the access for those users. Domain Controller is an important server and primary target for attackers, because it holds the key to the Active Directory environment. Every domain has atleast one domain controller (can have additional domain controllers as well).
To check the domain controller, we can use below command:
PS C:\Users\scarred.monk> (Get-ADDomainController).HostName RDSEDC01.rootdse.lab
Domain controllers provide the name resolution service and are responsible for keeping the domain database up to date with the information about the domain objects. Active directory database is stored in the file **C:\Windows\NTDS\ntds.dit** which is maintained in the domain controller. If this file gets stolen, all the information about the Active Directory objects like users, computers, groups, GPOs etc. including users credentials is also compromised.
Read-only Domain Controller
There are three types of domain controllers namely Primary domain controller, Read only domain controller(s) and additional domain controller(s) for backup purposes. Read-Only Domain Controllers (RODC) don’t allow any changes to the database. In case of Read-only domain controller, changes must be made on a writable domain controller and then replicated to the Read-only domain controller in a particular domain. Read-only domain controllers were made to address issues that are commonly found in branch offices in remote locations that might not have a domain controller, or with poor physical security, poor network bandwidth, or no local expertise to support it. The primary purpose of a Read-only Domain Controller is to facilitate for authentication from remote office branches and allow users to access domain resources.
Domain Tree
Domain tree is represented as a series of domains connected together in a hierarchical order that use the same DNS namespace. When we add a child domain to a parent domain, a domain tree is created. For example- there is a root domain rootdse.lab, and a new domain matrix (FQDN is matrix.rootdse.lab) is added to it, then it becomes a part of same domain tree once trust is automatically created between both of them. Trust is explained in the next section.
Forest
Active directory forest is a collection of multiple domain trees that share a common schema and all domains are connected together through a trust. Each domain in the forest can have one or more Domain controllers which can interact with other domains and can access the resources from other domains as well. The name of the forest is the same as the root domain. If a forest contains a single domain, then that domain itself is the root domain.
We can check the forest name in Active Directory as follows:
PS C:\Users\scarred.monk> Get-ADForest
ApplicationPartitions : {DC=DomainDnsZones,DC=matrix,DC=rootdse,DC=lab, DC=ForestDnsZones,DC=rootdse,DC=lab, DC=DomainDnsZones,DC=rootdse,DC=lab}
CrossForestReferences : {}
DomainNamingMaster : RDSEDC01.rootdse.lab
Domains : {matrix.rootdse.lab, rootdse.lab}
ForestMode : Windows2016Forest
GlobalCatalogs : {RDSEDC01.rootdse.lab, MTRXDC01.matrix.rootdse.lab}
Name : rootdse.lab
PartitionsContainer : CN=Partitions,CN=Configuration,DC=rootdse,DC=lab
RootDomain : rootdse.lab
SchemaMaster : RDSEDC01.rootdse.lab
Sites : {Default-First-Site-Name}
SPNSuffixes : {}
UPNSuffixes : {}
The above command can be filtered to extract the forest name by requesting the RootDomain property from the above output:
PS C:\Users\scarred.monk> (Get-ADForest).RootDomain rootdse.lab
In the same way, we can use this method to view any specific property, by having the whole command in parenthesis and type the property name you want to view.
Trusts
In a forest, domains are interconnected by connections called as trusts. This is why the users from a domain are able to access resources of other domains. In an Active Directory environment, once a trust is established between two domains, it grants access to resources to the users, groups and computers across entities. This is done by linking up the authentication systems between the domains and allowing authentication traffic to flow between them. This will be discussed in detail later to understand what happens when a user from a domain requests access to a resource of another domain, the current domain controller returns the user with a special ticket (signed with inter-realm trust key) that referrs to the domain controller of another domain. Don’t worry, if this doesn’t make sense now, this will be explained in detail later in Kerberos section.
Trust direction (One-way or two way)
Trusts can be one-way or two-way. In one-way trust Domain one trusts Domain two which means that Domain one is the trusting domain and Domain two will be the trusted domain. For a user in a certain domain to access a resource in another domain, the user needs to be in the trusted domain. Below diagram shows a graphical representation of the trust flow between two domains.
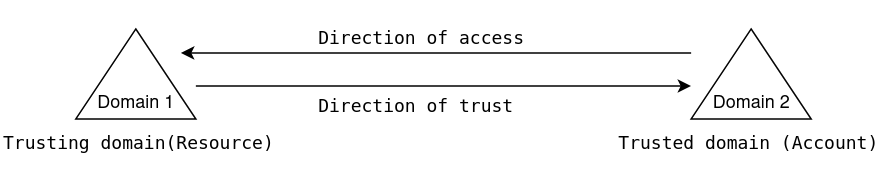
In case of two-way trust, all domains are allowed to share resources to all users regardless of which domain they belong to. As the name suggests, the trust works in both directions. When we create a trust between two domains (Domain one and Domain two), user accounts in Domain one will have access to resources in Domain two and vice-versa.
There are various types of trust. Trusts can be transitive or non-transitive. Below table explains the different types of trusts.
| Trust Type | Property | Trust Direction | Auth. | Details |
|---|---|---|---|---|
| Tree-Root | Transitive | Two-way | Kerberos V5 or NTLM | Created automatically when a new Tree is added to a forest |
| Parent-Child | Transitive | Two-way | Kerberos V5 or NTLM | Created automatically when a child domain is added |
| Shortcut | Transitive | One-way or Two-way | Kerberos V5 or NTLM | Created Manually. Used in a forest to shorten the trust path to improve authentication times |
| Forest | Transitive | One-way or Two-way | Kerberos V5 or NTLM | Created Manually.Used to share resources between AD DS forests. |
Transitive Trust in a forest:-
A Transitive Trust extends to any other trusted domain in the forest.
For example:-
If Domain one trusts Domain two, and Domain two trusts Domain three then, Domain one trusts Domain three.
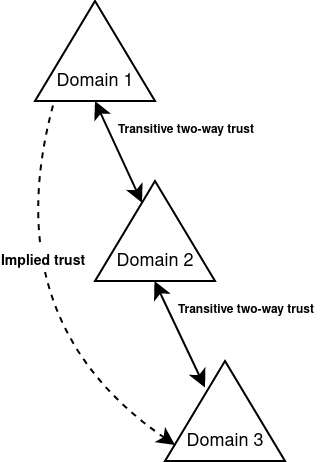
Here, the trust relationship passes through each trusted domain. And because it is transitive trust, it allows the user accounts in Domain one to access resources in Domain three and vice-versa (without having to create an additional trust between Domain one and Domain three)
Non-transitive Trust in a forest:-
In case of non-transitive trust, the relationship to domains outside of the trust is restricted. This means that the other domains are not allowed to access resources outside of the trust. They won’t be able to pass through their authentication information.
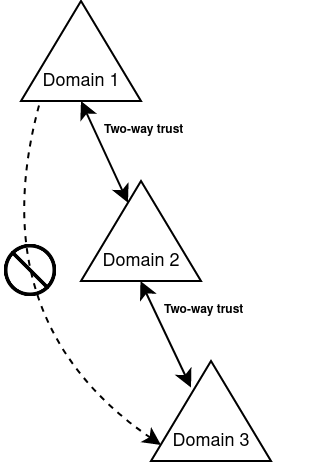
Here in the above example, a non-transitive trust relationship is established between Domain one and Domain two, and the user accounts in both domains have access to resources in the other domain. So when we add a new Domain three and create a trust between Domain two and Domain three, users in Domain one are not automatically allowed access to resources in Domain three.
Automatic Trusts in forest:-
By default, two-way, transitive trusts are created automatically when a child domain is added or when a domain tree is added. The two default trust types are parent-child trusts and tree-root trusts.
Global Catalog (GC)
Global catalog is used to perform forest wide searches since the Global Catalog server contains a full replica of all the objects. The root domain controller in a domain is considered as the Global Catalog server by default. To speed up the queries for the objects in other domains of the forest, a global catalog server has replica of its own domain and read-only partitions with objects of other domains. Let’s suppose that we have to query the Description attribute of a specific user from the domain other than the current one, in that case global catalog will retrieve it without requiring to query the Domain Controller of the other domain.
Let’s take an example of an Active Directory forest having four domains where Domain one is the Root domain:
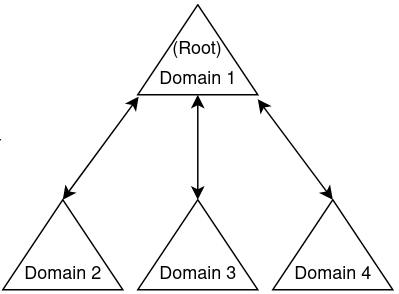
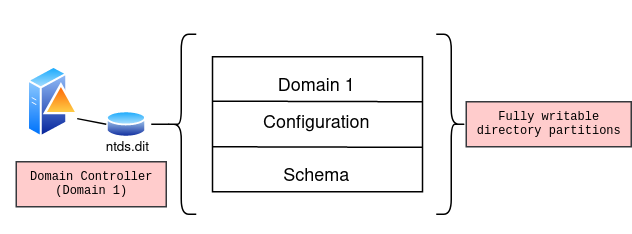
Since Domain one is the root domain controller, it holds the fully writable directory partition of the current domain:
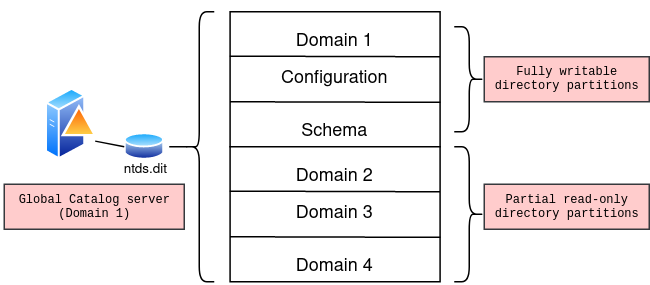
The global catalog server holds the replica of its own domain (full and writable) and the partial, read-only replica of all other domains in the forest in the directory database file (Ntds.dit) :
Summary 📓
- Active Directory is a Directory service that acts as a centralised repository and holds all the data related to Active Directory objects
- Active Directory Domain is a structure of all objects like users, computers, groups etc sharing an Active Directory database
- Domains represent logical partitions within an Active Directory forest
- SID (Security Identifier) is used to uniquely identify security principals like user, computer accounts etc.
- RID (Relative identifier) is the last part of SID, that uniquely identifies an account or group within a domain
- Fully Qualified Domain name is the complete domain name for a specific host in a domain
- Domain tree is basically a series of domains connected together in a hierarchical order
- Domain Controller authenticates and validates the user access on the network
- Trust allows users, groups and computers to access resources from other entities
- Global catalog contains full replica of all objects and is used when forest wide searches are performed
In part 2 we’ll cover the different types of Active directory objects and how to query them.
