In this blogpost, we’ll discuss about different Active directory objects and basic concepts like :
- Why Active Directory objects are required in a domain
- How they can be created
- How to enumerate the Active directory objects
Active Directory Objects
Active Directory objects are a set of attributes which represent a resource in a domain. Each Active Directory object is identified by a unique SID (Security Identifier) which is used to allow or deny access to various resources in the domain. Let’s discuss about few of the AD objects which are part of the Active directory.
User Objects
User objects are assigned to the Domain user accounts and are used to gain access to domain resources. These are managed from the Active Directory Users and Computers console if you have the required rights to manage the user objects. User accounts are also used to run programs or system services and are identified by user SID which is similar to the domain SID, and it’s combination of the domain SID and user RID (Relative Identifier).
PS C:\Users\scarred.monk> Get-ADUser Scarred.Monk
DistinguishedName : CN=Scarred Monk,CN=Users,DC=rootdse,DC=lab
Enabled : True
GivenName : Scarred
Name : Scarred Monk
ObjectClass : user
ObjectGUID : 2ba8220b-63db-4dda-b6de-095a7fa0da24
SamAccountName : Scarred.Monk
SID : S-1-5-21-580985966-2115238843-2989639066-1107
Surname : Monk
UserPrincipalName : Scarred.Monk@rootdse.lab
SID of User Object
In the user’s SID value, S-1-5-21-580985966-2115238843-2989639066 is the domain SID (Security Identifier) and 1107 is the user RID (Relative identifier) which uniquely identifies it.
A SID can be divided as follows:
(SID)-(Revision Level)-(Identifier-Authority)-(Sub-Authority1)-(Sub-Authority2)...-(RID)
Microsoft has explained the SID components as follows:
- SID:
Sin the SID identifies the above string as being an SID. - Revision level: The Revision level of the SID structure. To date, this has never changed and has always been
1. - Identifier-Authority: A 48-bit identifier authority value that identifies the authority that issued/created the SID. (In our case, the value of identifier-authority is 5
(SECURITY_NT_AUTHORITY)) - Subauthority: This is a variable number that identifies the relation of the user or group described by the SID to the authority that created it.
- RID: Relative identifier (RID) is a variable number of subauthority value that uniquely identify the trustee relative to the authority that issued the SID.
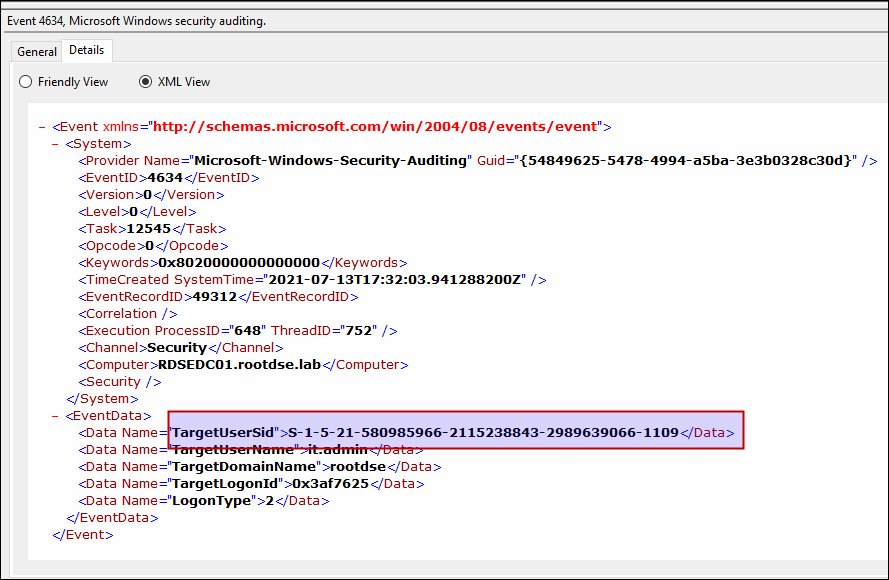
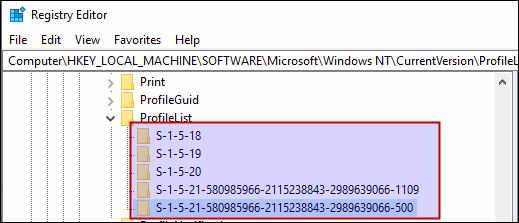
While working in a Domain environment, you’ll see user SID at multiple places like in event viewer or in ACLs. SID is also used in security descriptors to store information related to the permissions.
Below is an example of User SID in event logs:
Below is an example of User SID in Registry:
You can find a list of different Well-Known SIDs here at Microsoft Docs.
However, In an enterprise environment, a user can have more than one user accounts to do different tasks. For example, System Administrators in an organisation can have multiple different accounts, like one account for working on the laptop assigned to them, second account to work in the local domain and few more accounts to work on other domains in the Active Directory forest.
To get details of all the user accounts in Active directory domain, we can use below command:
PS C:\Users\scarred.monk> Get-ADUser -Filter *
The output of this command is usually huge as it contains lot of details about all the users. To just get few properties of users, we can use the Select-Object cmdlet (it has the alias of Select) to select only the properties that we are interested in like SamAccountName, SID, enabled (to see if account is enabled/disabled)
PS C:\Users\scarred.monk> Get-ADUser -f * |select SamAccountName, SID, enabled SamAccountName SID enabled -------------- --- ------- Administrator S-1-5-21-580985966-2115238843-2989639066-500 True Guest S-1-5-21-580985966-2115238843-2989639066-501 False krbtgt S-1-5-21-580985966-2115238843-2989639066-502 False MATRIX$ S-1-5-21-580985966-2115238843-2989639066-1103 True darkvortex$ S-1-5-21-580985966-2115238843-2989639066-1104 True SQLServiceAccount S-1-5-21-580985966-2115238843-2989639066-1105 True Scarred.Monk S-1-5-21-580985966-2115238843-2989639066-1107 True
The Filter parameter used here is to get all the users. Filter parameter uses the PowerShell Expression Language to write query strings for Active Directory.
-Filter can be used as -F
Below is an example to use Filter parameter to find user accounts that start with admin*
PS C:\Users\scarred.monk> Get-ADUser -Filter 'Name -like "admin*"' DistinguishedName : CN=Administrator,CN=Users,DC=rootdse,DC=lab Enabled : True GivenName : Name : Administrator ObjectClass : user ObjectGUID : 061b1157-9a8d-4a34-9304-563a08e3883c SamAccountName : Administrator SID : S-1-5-21-580985966-2115238843-2989639066-500
When you log in as a domain user, the domain computer (on which login attempt is made) sends the request to the domain controller for authentication and asks the domain controller what privileges are assigned for the user account. After validation, the computer receives a response from the domain controller, and it logs you in with the proper permissions and restrictions. This happens because the credentials information for domain user accounts is stored on the domain controller instead of the local computer on which the user is logging into.
To create a new user, we can use New-ADUser cmdlet:
PS C:\> New-ADUser -Name "AD User" -GivenName AD -Surname User -SamAccountName ad.user -UserPrincipalName ad.user@rootdse.org -AccountPassword (ConvertTo-SecureString password@123 -AsPlainText -Force) -PassThru
Computer Objects
Computer object represents the machine that is joined to the domain and used by the users to login into the domain. When a user is logged into the computer as a domain user, the computer object acts as a medium to authenticate the user to domain. So if the computer object is removed from the domain, user will not be able to log in because the computer will not be able to access the domain controller.
PS C:\Users\scarred.monk> Get-ADComputer -f * DistinguishedName : CN=RDSEDC01,OU=Domain Controllers,DC=rootdse,DC=lab DNSHostName : RDSEDC01.rootdse.lab Enabled : True Name : RDSEDC01 ObjectClass : computer ObjectGUID : 032428f5-d629-451b-9d1d-46fce3ec0677 SamAccountName : RDSEDC01$ SID : S-1-5-21-580985966-2115238843-2989639066-1000 UserPrincipalName : DistinguishedName : CN=SQLSERVER,CN=Computers,DC=rootdse,DC=lab DNSHostName : Enabled : True Name : SQLSERVER ObjectClass : computer ObjectGUID : d4a1bca9-d729-4d61-90d3-ff33ea9f0c1e SamAccountName : SQLSERVER$ SID : S-1-5-21-580985966-2115238843-2989639066-1106
All computer objects have their own machine user account that ends with $
For example: machine account of the computer object RDSEDC01 is RDSEDC01$. These accounts perform their own actions in the domain.
A Domain has three types of objects that can be counted as computer objects:
- Domain Controllers
- Domain Computers (Workstations)
- Member servers
Domain Controllers
Domain Controller is a centralized windows server that manages the domain by hosting the Active Directory domain and by providing authentication and directory services to clients. A Domain Controller can only process authentication requests for a single domain, but it can also store partial read-only copies of objects from other domains in the forest (if it is enabled as a Global Catalog server).
To check the domain controller, we can use below command:
PS C:\Users\scarred.monk> Get-ADDomainController
ComputerObjectDN : CN=RDSEDC01,OU=Domain Controllers,DC=rootdse,DC=lab
DefaultPartition : DC=rootdse,DC=lab
Domain : rootdse.lab
Enabled : True
Forest : rootdse.lab
HostName : RDSEDC01.rootdse.lab
InvocationId : 85a56dee-48fe-4897-8941-50ed5a196849
IPv4Address : 192.168.209.110
IPv6Address :
IsGlobalCatalog : True
IsReadOnly : False
LdapPort : 389
Name : RDSEDC01
NTDSSettingsObjectDN : CN=NTDS Settings,CN=RDSEDC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=rootdse,DC=lab
OperatingSystem : Windows Server 2019 Datacenter
OperatingSystemHotfix :
OperatingSystemServicePack :
OperatingSystemVersion : 10.0 (17763)
OperationMasterRoles : {SchemaMaster, DomainNamingMaster, PDCEmulator, RIDMaster...}
Partitions : {DC=ForestDnsZones,DC=rootdse,DC=lab, DC=DomainDnsZones,DC=rootdse,DC=lab, CN=Schema,CN=Configuration,DC=rootdse,DC=lab, CN=Configuration,DC=rootdse,DC=lab...}
ServerObjectDN : CN=RDSEDC01,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=rootdse,DC=lab
ServerObjectGuid : d50faf97-ee22-4724-b248-bf8eeda85c92
Site : Default-First-Site-Name
SslPort : 636
Domain Computers (Workstations)
Domain Computers can be represented by the personal computers used by employees like desktops, laptops that are a part of domain. In terms of Active Directory, computers objects are very similar to user objects, because computer objects possess all of the attributes of user objects (computer objects inherit directly from the user object class). There are few reasons for the Computers to be represented in the Active Directory like the need to access resources securely, utilize GPOs, and have permissions assigned to them.
object classes will be explained in detail in the upcoming blogpost related to AD schema and LDAP
In order to join an Active Directory domain and allow the domain users to login to it, domain computers require a secure channel to communicate to a domain controller. A secure channel means an authenticated connection that can transmit encrypted data. To create the secure channel, the domain computer must present the domain computer account’s password to the domain controller. Similar to the user account authentication, Active Directory uses the Kerberos authentication to verify the identity of a computer account. The domain controller verifies a trusted domain computer by the associated computer object and its stored password.
To check the domain computers, we can use below command:
PS C:\Users\scarred.monk> Get-ADComputer -Filter *
Member servers
Member servers in a domain environment offer different services. These servers have one or more roles installed for the type of service they are required to offer such as Exchange server, Web server, File server, SQL server etc. They can have Windows Server OS or Linux OS as well.
To check the member servers, we can use below command:
PS C:\Users\scarred.monk> Get-ADComputer -Filter 'operatingsystem -like "*server*"'
Let’s talk about next type of AD Object, which is group object.
Group Objects
Group objects are used to contain a number of different Active Directory Objects such as users, computers and other groups as well. This is done in order to make the administration easier for System Administrators by assigning permissions to a group of users/computers rather than the individual accounts, creating delegation Group Policies for a group, creating email distribution lists etc.
For example, in an organisation, there are different groups for different teams, and different permissions are assigned to these groups as per the requirement. Let’s say there is a group called as “DB Admins” which has access to login and perform few database operations on multiple SQL servers, accessing multtiple DB file shares, and so on. When new users join the DB team, IT team adds the user into that group (DB ADmins) which will give the new users all the access that their team members have. It saved the IT team time to work on providing each user access to all the resources individually.
To get details of all the groups in Active directory domain, we can use below command:
PS C:\Users\scarred.monk> Get-ADGroup -f * | Select-Object name
name
----
Administrators
Users
Guests
Print Operators
Backup Operators
Replicator
Remote Desktop Users
Network Configuration Operators
Performance Monitor Users
Performance Log Users
Distributed COM Users
IIS_IUSRS
Cryptographic Operators
Event Log Readers
Certificate Service DCOM Access
RDS Remote Access Servers
RDS Endpoint Servers
RDS Management Servers
Hyper-V Administrators
Access Control Assistance Operators
Remote Management Users
Storage Replica Administrators
Domain Computers
Domain Controllers
Schema Admins
Enterprise Admins
Cert Publishers
Domain Admins
Domain Users
Domain Guests
Group Policy Creator Owners
RAS and IAS Servers
Server Operators
Account Operators
Pre-Windows 2000 Compatible Access
Incoming Forest Trust Builders
Windows Authorization Access Group
Terminal Server License Servers
Allowed RODC Password Replication Group
Denied RODC Password Replication Group
Read-only Domain Controllers
Enterprise Read-only Domain Controllers
Cloneable Domain Controllers
Protected Users
Key Admins
Enterprise Key Admins
DnsAdmins
DnsUpdateProxy
Types of groups
Distribution Group
Distribution Group is used to include multiple users in a group. When an email is sent to a distribution group, it is sent to all of the users in that Distribution group. For example: Distribution Group with name Corporate Office will include all users from corporate office. When someone sends an email to that group, it’ll be delivered to all corporate office employees.
Security Group
Similar to Distribution group, a security group can contain user/computer accounts or groups that are used to provide different access and permissions across the domain/forest to the users/computers in group. For example, a security group named as DBAdmins can contain all members of the Database Operation Team which might have access to multiple SQL servers and file shares for DB team. When a new DB Admin joins the team, adding the user account into the DBAdmins security group would provide all rights across the SQL Databases.
To get details about the security groups, we can use filter like GroupCategory -eq "security":
PS C:\Users\scarred.monk> Get-ADGroup -Filter {GroupCategory -eq "security"}
There are three group scopes for each group type:
- Domain local: Used to manage access permissions to different domain resources only in the domain where it was created.
- Global: Used to provide access to resources in another domain. A global group can be added to other global and local groups.
- Universal: Used to define roles and manage resources that are distributed across multiple domains. If a network has multiple branches connected, it is desirable to use universal groups only for rarely changing groups.
Some important groups in Active Directory are as follows :
Admin groups
Most important groups are Domain Admins and Enterprise Admins:
- Domain Admin group provides administrator privileges to its members in the domain.
- Enterprise Admins group provides administrator privileges in the whole forest.
Other important groups in AD
In addition to these two important groups, there are other important groups as well which you should be aware of:
- Schema Admins: The members of the Schema Admins group can modify the Active Directory database schema.
-
DNSAdmins: Members of DNSAdmins group have permissions to access/modify network DNS information if the DNS server role is installed on a domain controller in the domain. Shay Ber has published a post that explains how the members of DNSAdmins group can execute code (arbitrary DLL) in Domain Controllers as SYSTEM user.
- Print Operators: If you add a user in the
Print Operatorsgroup, that user account can login into the Domain Controllers. - Protected Users: The Protected Users group allows to enforce the security of accounts. The members of this group are afforded additional protections against the compromise of credentials during authentication processes.
- Members of protected users group are not allowed to authenticate with NTLM
- Unable to use DES or RC4 encryption types in Kerberos pre-authentication (Will be explained in Kerberos blogpost)
- They cannot be delegated with Kerberos unconstrained or constrained delegation (Will be explained in Kerberos blogpost)
- Unable to renew the Kerberos Ticket Granting Tickets (TGTs) beyond the initial four-hour lifetime
- Server Operators: The members of the Server Operators group can log on to Domain Controllers and manage its configuration.
- Account Operators: The members of the Account Operators group can create and modify most types of accounts, including those of users, local groups, and global groups, and members can log in locally to domain controllers. However, members of the Account Operators group cannot manage the Administrator user account, or the Administrators, Server Operators, Account Operators, Backup Operators, or Print Operators groups.
- Backup Operators: The members of Backup Operators have the rights to login, take back up, restore/modify files in Domain Controllers.
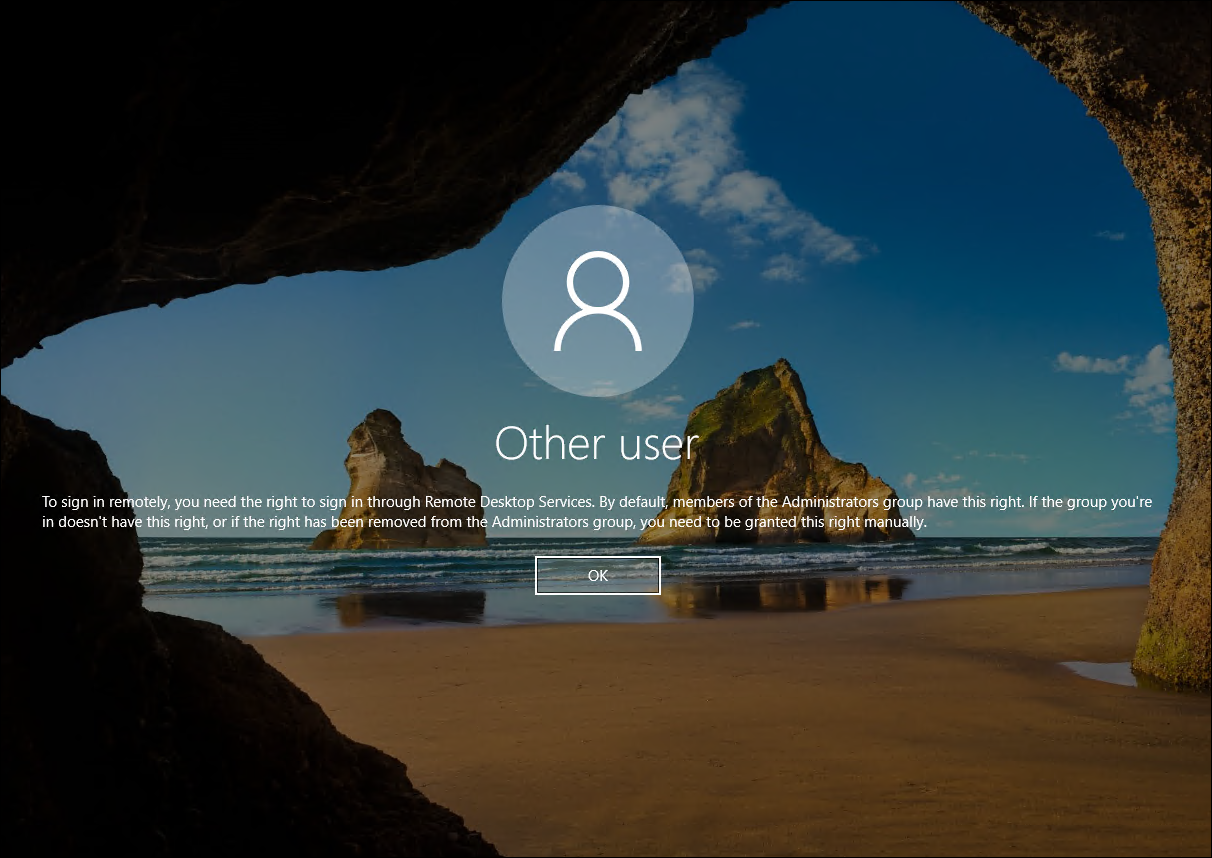
- Remote Desktop Users: The members of this group can log on to a Domain Controller through RDP. If a user already has access to login into Domain Controller locally, then adding it to this group can allow the user to login on Domain Controller remotely through RDP. If local login is not enabled and added to this group, then you’ll see below warning.
- Group Policy Creator Owners: The members of Group Policy Creator Owners can edit GPOs in a domain.
Below are some high-value groups. The members from these groups have the permissions by default to login into Domain Controllers. If an account from these groups is compromised, then there are high chances for the AD domain to be compromised.
Administrators
Domain Admins
Enterprise Admins
Print Operators
Backup Operators
Account Operators
Custom groups
In addition to this, organizations also create custom privileged groups like for IT Admins, IT helpdesk, SQL admins, Application admins and so on. Also, groups are created if we add additional roles into the server. Like when we add DHCP role, DHCP Administrators group is created or when Microsoft exchange is installed, exchange organization administrators and Exchange Windows Permissions groups are added. To get detailed information, there are many other groups described in Microsoft docs
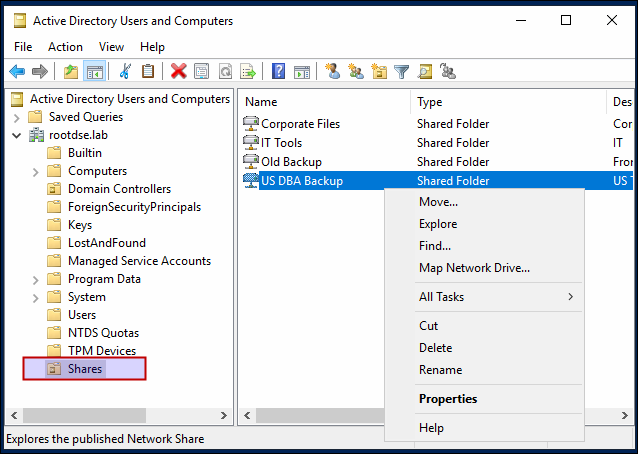
Shared Folders
Shared folders are also objects in Active Directory. When a new share is published in AD, an object is created for it. This can be very helpful for the AD users to find all the shares easily. Below is screenshot of published shared folders in AD:
For pentesters, shares can be enumerated to see which ones are accessible and what data is stored there. We can enumerate shares as follows:
PS C:\> Get-SmbShare Name ScopeName Path Description ---- --------- ---- ----------- ADMIN$ * C:\Windows Remote Admin C$ * C:\ Default share Corporate Files * C:\ADShares\Corporate Files Corporate Files data for 2020 DBA Backup * C:\ADShares\DBA Backup Romania DB Backup IPC$ * Remote IPC IT Tools * C:\ADShares\IT Tools IT Team Important Tools NETLOGON * C:\Windows\SYSVOL\sysvol\rootdse.org\SCRIPTS Logon server share Old Backup * C:\ADShares\Old Backup All Backup Operations Team * C:\ADShares\Operations Team Engineering Operations daily data Salary Details * C:\ADShares\Salary Details Finance Team 2020 Sales Data * C:\ADShares\Sales Data Latest Sales Team Shared folder SYSVOL * C:\Windows\SYSVOL\sysvol Logon server share PS C:\> net view \\RDSEDC01 Shared resources at \\RDSEDC01 Share name Type Used as Comment ------------------------------------------------------------------------------- Corporate Files Disk Corporate Files data for 2020 DBA Backup Disk Romania DB Backup IT Tools Disk IT Team Important Tools NETLOGON Disk Logon server share Old Backup Disk All Backup Operations Team Disk Engineering Operations daily data Salary Details Disk Finance Team 2020 Sales Data Disk Latest Sales Team Shared folder SYSVOL Disk Logon server share The command completed successfully.
In part 3, we’ll cover the Group policy, which is one of the important elements of Active Directory. We’ll discuss what group policies are, why they are required, how to create them, what can be accomplised using Group policies and also see how group policies can be enumerated and compromised.